Overnight, Apple has pushed two updates, to the data files used by XProtect, bringing its version number to 2144 dated 15 April 2021, and to its malware removal tool MRT, bringing it to version 1.77, also dated 15 April 2021.
However, XProtect, Gatekeeper and MRT.app use a variety of formats (XML, SQL and machO binary, respectively) to store data, and they also use different forms of obfuscation within those formats. In this post, we’ll start with looking at how to extract data and run diffs on Apple’s Malware Removal Tool, aka the MRT.app. Sleep tracking with Apple Watch is a great way to gain new insight into your sleeping habits and trends over time. In fact, with the release of watchOS 7 last fall, Apple officially added native. Method 4: Run MRT as an Administrator. If all of the methods above don’t work, you can try forcing MRT to run with administrator permissions. Step 1: Locate the mrt.exe file by right-clicking its entryon the Desktop window and choose Properties. Mrt free download - MRT Mixer, MRT Lock, MRT Player, and many more programs. MacRumors attracts a broad audience of both consumers and professionals interested in the latest technologies and products. We also boast an active community focused on purchasing decisions and technical aspects of the iPhone, iPod, iPad, and Mac platforms.
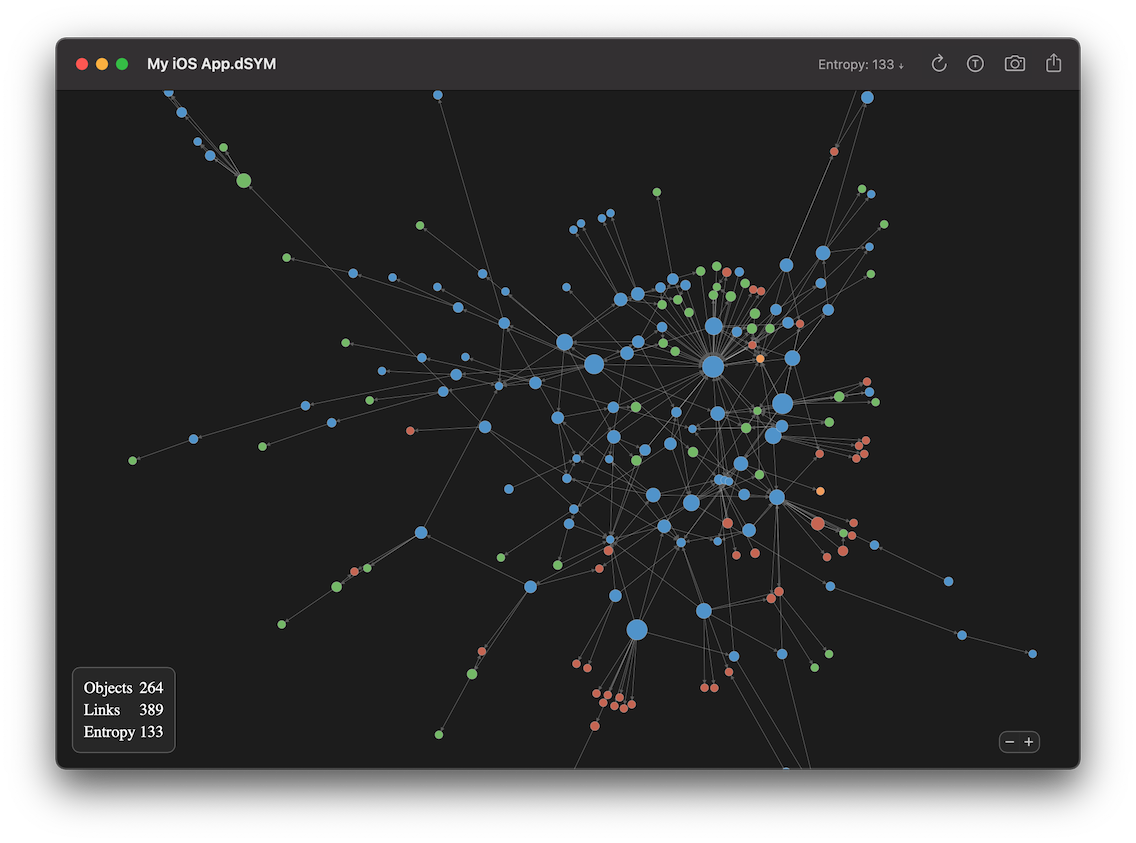
Apple doesn’t release information about what these updates add or change, and obfuscates the identities of most malware detected by XProtect using internal code names.
Mrt App Reddit Machine
Changes found in the XProtect Yara definitions include the addition of new signatures for MACOS.ef3df25 (Bundlore Script), MACOS.11eaac1 (VindInstaller.B), MACOS.0e32a32 (Bundlore Script) and MACOS.6eaea4b (XCSSET variants, which Apple names DUBROBBER.E). There are also changed signatures for MACOS.2afe6bd (Adload), MACOS.4d60c89 (Notarized Shlayer: DLVPlayer), MACOS.1db9cfa (XCSSET variants, which Apple names DUBROBBER.E). There’s been a lot of cleaning up of whitespace from the previous definitions, and Apple has added comments identifying MACOS.2070d41 as DUBROBBER.A, MACOS.9e2bab9 as DUBROBBER.B, MACOS.889c9e6 as DUBROBBER.C, and MACOS.1db9cfa as DUBROBBER.D.
You can check whether this update has been installed by opening System Information via About This Mac, and selecting the Installations item under Software.
Mrt App Reddit Macbook

A full listing of security data file versions is given by SilentKnight, LockRattler and SystHist for El Capitan, Sierra, High Sierra, Mojave, Catalina and Big Sur, available from their product page. If your Mac has not yet installed this update, you can force an update using SilentKnight, LockRattler, or at the command line.
I have updated the reference pages here which are accessed directly from LockRattler 4.2 and later using its Check blog button.
I maintain lists of the current versions of security data files for Big Sur on this page, Catalina on this page, Mojave on this page, High Sierra on this page, Sierra on this page, and El Capitan on this page.
Mrt App Reddit Macro
I am grateful to Phil Stokes at Sentinel Labs for decoding of the obfuscated malware names here.