
- Forescout Secureconnector Windows Download
- What Is Forescout Secure Connector
- Forescout Secure Connector Mac Mode
Forescout Secureconnector Windows Download

Findings (MAC III - Administrative Sensitive)
| Finding ID | Severity | Title | Description |
|---|---|---|---|
| V-233333 | High | Forescout that stores device keys must have a key management process that is FIPS-approved and protected by Advanced Encryption Standard (AES) block cipher algorithms. | The NAC that stores secret or private keys must use FIPS-approved key management technology and processes in the production and control of private/secret cryptographic keys. Private key data is ... |
| V-233312 | High | If a device requesting access fails Forescout policy assessment, Forescout must communicate with other components and the switch to either terminate the session or redirect the endpoint to the remediation subnet. | Endpoints with identified security flaws and weaknesses endanger the network and other devices on it. Isolation or termination prevents traffic from flowing with traffic from endpoints that have ... |
| V-233311 | High | For endpoints that require automated remediation, Forescout must be configured to redirect endpoints to a logically separate VLAN for remediation services. | Automated and manual procedures for remediation for critical security updates will be managed differently. Continuing to assess and remediate endpoints with risks that could endanger the network ... |
| V-233310 | High | Endpoint policy assessment must proceed after the endpoint attempting access has been identified using an approved identification method such as IP address. | Automated policy assessments must reflect the organization's current security policy so entry control decisions will happen only where remote endpoints meet the organization's security ... |
| V-233315 | High | Forescout appliance must not be configured to implement a DHCP layer 3 method for separation or device authorization. | An internal rogue device can still bypass the authentication process, regardless of the policy flow. Configuring the NAC to process all device authentication will ensure that any rogue device, ... |
| V-233314 | High | Forescout must be configured so that all client machines are assessed by Forescout with exceptions that are allowed to bypass Forescout based on account or account type, as approved by the Information System Security Manager (ISSM) and documented in the System Security Plan (SSP). | The NAC gateway provides the policy enforcement allowing or denying the traffic to the network. Unauthorized traffic that bypasses this control presents a risk to the organization's data and ... |
| V-233318 | High | Forescout must place client machines on the blacklist and terminate Forescout agent connection when critical security issues are found that put the network at risk. | If a device communicates outside of its normal required communication, this could be suspect traffic and should be stopped and proper individuals notified immediately. |
| V-233340 | High | When connecting with endpoints, Forescout must validate certificates used for Transport Layer Security (TLS) functions by performing RFC 5280-compliant certification path validation. | A certificate's certification path is the path from the end entity certificate to a trusted root certification authority (CA). Certification path validation is necessary for a relying party to ... |
| V-233309 | High | Forescout must enforce approved access by employing admissions assessment filters that include, at a minimum, device attributes such as type, IP address, resource group, and/or mission conditions as defined in Forescout System Security Plan (SSP). | Successful authentication must not automatically give an entity access to an asset or security boundary. The lack of authorization-based access control could result in the immediate compromise and ... |
| V-233339 | Medium | Forescout must use a bidirectional authentication mechanism configured with a FIPS-validated Advanced Encryption Standard (AES) cipher block algorithm to authenticate with the endpoint device. | Bidirectional authentication provides stronger safeguards to validate the identity of other devices for connections that are of greater risk. Currently, DoD requires the use of AES for ... |
| V-233338 | Medium | Forescout must deny network connection for endpoints that cannot be authenticated using an approved method. | Without identifying devices, unidentified or unknown devices may be introduced, thereby facilitating malicious activity. Identification failure does not need to result in connection termination or ... |
| V-233331 | Medium | For TLS connections, Forescout must automatically terminate the session when a client certificate is requested and the client does not have a suitable certificate. | In accordance with NIST SP 800-52, the TLS server must terminate the connection with a fatal “handshake failure” alert when a client certificate is requested and the client does not have a ... |
| V-233330 | Medium | Forescout switch module must only allow a maximum of one registered MAC address per access port. | Limiting the number of registered MAC addresses on a switch access port can help prevent a CAM table overflow attack. This type of attack lets an attacker exploit the hardware and memory ... |
| V-233332 | Medium | Forescout must use TLS 1.2, at a minimum, to protect the confidentiality of information passed between the endpoint agent and Forescout for the purposes of client posture assessment. | Using older unauthorized versions or incorrectly configuring protocol negotiation makes the gateway vulnerable to known and unknown attacks that exploit vulnerabilities in this protocol. |
| V-233335 | Medium | Forescout must generate a log record when the client machine fails policy assessment because required security software is missing or has been deleted. | Generating log records with regard to modules and policies is an important part of maintaining proper cyber hygiene. Keeping and maintaining the logs helps to establish, correlate, and investigate ... |
| V-233334 | Medium | Communications between Forescout endpoint agent and the switch must transmit access authorization information via a protected path using a cryptographic mechanism. | Forescout solution assesses the compliance posture of each client and returns an access decision based on configured security policy. The communications associated with this traffic must be ... |
| V-233337 | Medium | Forescout must perform continuous detection and tracking of endpoint devices attached to the network. | Continuous scanning capabilities on the NAC provide visibility of devices that are connected to the switch ports. The NAC continuously scans networks and monitors the activity of managed and ... |
| V-233336 | Medium | Forescout must be configured with a secondary log server, in case the primary log is unreachable. | It is critical for the appropriate personnel to be aware if a system is at risk of failing to process audit logs as required. Without this notification, the security personnel may be unaware of an ... |
| V-233313 | Medium | Forescout must be configured to notify the user before proceeding with remediation of the user's endpoint device when automated remediation is used. | Connections that bypass established security controls should be allowed only in cases of administrative need. These procedures and use cases must be approved by the Information System Security ... |
| V-233317 | Medium | When devices fail the policy assessment, Forescout must create a record with sufficient detail suitable for forwarding to a remediation server for automated remediation or sending to the user for manual remediation. | Notifications sent to the user and/or network administrator informing them of remediation requirements will ensure that action is taken. |
| V-233316 | Medium | Forescout must send an alert to the Information System Security Manager (ISSM) and System Administrator (SA), at a minimum, when critical security issues are found that put the network at risk. | Requiring authentication and authorization of both the user's identity and the identity of the computing device is essential to ensuring a non-authorized person or device has entered the network. |
| V-233319 | Medium | Forescout must be configured so client machines do not communicate with other network devices in the DMZ or subnet except as needed to perform a client assessment or to identify itself. | Devices not compliant with DoD secure configuration policies are vulnerable to attack. Allowing these systems to connect presents a danger to the enclave.Verify that Forescout is not allowed to ... |
| V-233326 | Medium | Forescout must authenticate all endpoint devices before establishing a connection and proceeding with posture assessment. | Authenticating all devices as they connect to the network is the baseline of a good security solution. This is especially important prior to posture assessment to ensure authorized devices are ... |
| V-233327 | Medium | Forescout must be configured to apply dynamic ACLs that restrict the use of ports when non-entity endpoints are connected using MAC Authentication Bypass (MAB). | MAB is only one way of connecting non-entity endpoints, and can be defeated by spoofing the MAC address of an assumed authorized device. By adding the device to the MAB, the device can then gain ... |
| V-233324 | Medium | Forescout must off-load log records onto a different system. | Having a separate, secure location for log records is essential to the preservation of logs as required by policy. |
| V-233325 | Medium | Forescout must generate a critical alert to be sent to the Information System Security Officer (ISSO) and Systems Administrator (SA) (at a minimum) in the event of an audit processing failure. | Ensuring that a security solution alerts in the event of misconfiguration or error is imperative to ensuring that proper auditing is being conducted. Having the ability to immediately notify an ... |
| V-233322 | Medium | Forescout must deny or restrict access for endpoints that fail critical endpoint security checks. | Devices that do not meet minimum-security configuration requirements pose a risk to the DoD network and information assets.Endpoint devices must be disconnected or given limited access as ... |
| V-233323 | Medium | Forescout must be configured to log records onto a centralized events server. | Keeping an established, connection-oriented audit record is essential to keeping audit logs in accordance with DoD requirements. |
| V-233320 | Medium | Forescout must enforce the revocation of endpoint access authorizations when devices are removed from an authorization group. | Ensuring the conditions that are configured in policy have proper time limits set to reflect changes will allow for proper access. This will help to validate that authorized individuals have ... |
| V-233321 | Medium | Forescout must enforce the revocation of endpoint access authorizations at the next compliance assessment interval based on changes to the compliance assessment security policy. | This requirement gives the option to configure for automated remediation and/or manual remediation. A detailed record must be passed to the remediation server for action. Alternatively, the ... |
| V-233328 | Medium | Forescout must reveal error messages only to the Information System Security Officer (ISSO), Information System Security Manager (ISSM), and System Administrator (SA). | Ensuring the proper amount of information is provided to the Security Management staff is imperative to ensure role based access control. Only those individuals that need to know about a security ... |
| V-233329 | Medium | Forescout must configure TCP for the syslog protocol to allow for detection by the central event server if communications is lost. | It is critical for the appropriate personnel to be aware if a system is at risk of failing to process audit logs as required. Without this notification, the security personnel may be unaware of an ... |
Removal guide for software 'secureconnector.exe' on Windows (XP, Vista, Win7, Win8 and Windows 10) systems. Tips for getting it away from the hard disk
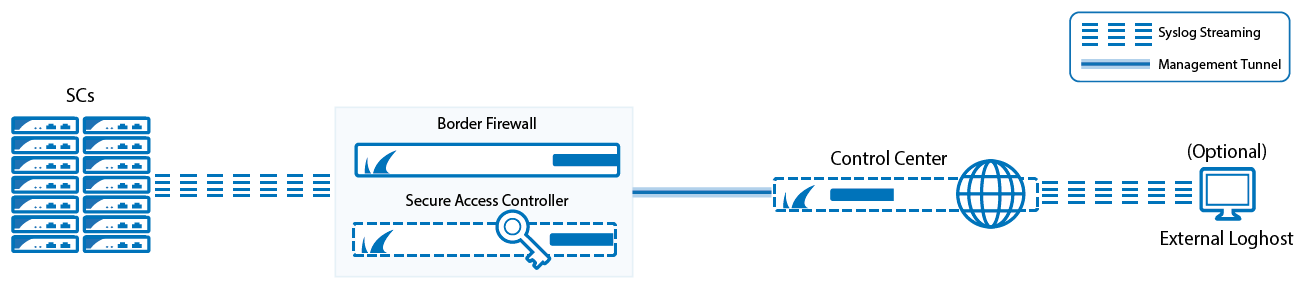
Press F3 key to open standard search window. Than type 'secureconnector.exe' into search box. In couple of minutes, seconds if you're lucky, Windows will find all the copies. Try to locate program, to which the process secureconnector.exe belongs. This is the network address of the Forescout Enterprise Manager or standalone Appliance. (The host on which the the Forescout Appliance is hosted.) For example, if the Forescout Appliance is hosted at the IP address 192.168.10.23, then you enter. Web API Username and Password.
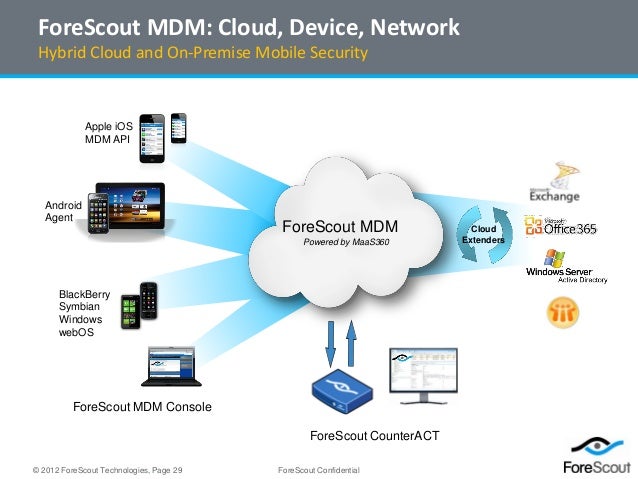
Forescout Secure Connector Mac Download Mac ForeScout, a multi-award winning automated network security platform, gives you real-time visibility and control over everything connecting to your network; all devices, all operating systems, all applications, all users. Zotero is a powerful, easy-to-use research tool that helps you gather, organize, and analyze sources and then share the results of your research.
How to permanently delete secureconnector.exe from your computer:
First, please read this important warning: This article shows a general guide how to remove any file from your computer. It DOES NOT implies that secureconnector.exe is harmful! Be aware of removing executable files from your computer without deeper knowledge of what you're doing. First of all, because of secureconnector.exe is an executable, there is always a possibility that removing this file MAY damage the operating system or even your data.
Are you still ready to remove secureconnector.exe? OK, let's go for it. Here is the guide:
- Create Restore point for Windows (not available in Windows XP). Restore point will help you to revert changes, if something'll go wrong.
- Press F3 key to open standard search window. Than type 'secureconnector.exe' into search box. In couple of minutes, seconds if you're lucky, Windows will find all the copies.
- Try to locate program, to which the process secureconnector.exe belongs. Than try to uninstall that program in a standard way.
For example, if secureconnector.exe is found in folder C:Program FilesDummy game**some subfolder**, it most probably belongs to 'Dummy game' software package. - If your problem persist and you are not able to remove file that way, go to the search results (step 2) and try to manually delete all the occurrences of secureconnector.exe.
Note: If the process is running, you will not be able to delete the file. In such situation, you must stop the process via Task manager (right click on Windows task bar, select 'Task manager'. In Task Manager windows, click 'Processes' pane. Than select secureconnector.exe and press 'Delete' key). Detailed guide. - Some malware can hide itself under different names (so-called 'clones'). To remove such self-hiding program, use specialized tool 'EasyRemove' - see below
What Is Forescout Secure Connector
EasyRemove is lightweight and easy-to-use removal tool for secureconnector.exe
Download EasyRemove and get your computer fixed within minutes.
You can be also interested in: checking if secureconnector.exe is virus or not , how to solve typical problems with secureconnector.exe error (or more specific secureconnector.exe application error) Solve problems with secureconnector.exe not responding. Typical Windows message: secureconnector.exe high cpu. How to handle damaged file: secureconnector.exe is corrupted.
Main article: secureconnector.exe
You know it: the longer you own your computer, the slower it runs and the more often it stucks.
EUROBYTE TOOLS speeds up more than 1 million computers around the world. Try it now:
Security risk rating: N/A
Note: The security risk rating is based on user's opinions. This is not our recommendation or adwice any way. Please use your own mind and think twice :-)
Trojan and malware info: N/A
Typical errors: File not found, An error occured in file, Not responding, Application Error 0x , Howto delete, stop, run, remove and find the file...
Notes:
- N/A is an abbreviation for 'Not available'. That means that now we have no information if this process is harmful or not.
- There is almost unlimited numbers of messages that should appear while you're running the software. We selected only the typical ones here
Related posts for secureconnector.exe
See Related Forum Messages: Follow the Links Below to View Complete Thread
Summary: 0 user rated this process.
Nameparts: se cureconnector, sec ureconnector, secu reconnector, secur econnector, secure connector, securec onnector, secureco nnector, securecon nector, secureconn ector, secureconne ctor, secureconnec tor, secureconnect or, .User reviews snapshot:
[22:24:06] kms-qad.exe: malware analiz...
[00:22:19] sandisksecureaccessv2_win.exe: how to restore the flasdisk sa...
[20:58:22] dx8vb.dll: the risk is virus ...
[14:18:21] nvspcaps.exe: NVIDIA Server Capture is neces...
[20:01:40] pcacli.dll: If you have a game or anything...
[22:42:35] half_life_2_lost_coast_gdf.dll: halmacpi.dll...
[06:33:34] nvgftraypluginr.dll: NvGFT Plugin.dll ...
[20:21:06] ivms-4200.exe: Process required for IVMS CCTV...
[19:16:19] pclink.exe: Wireless Printing software for...
[00:18:37] mcnetwork.dll: amze...
Warning: Once again about user reviews. Our users can freely add their reviews about whatever process they want. We, of course, purify and filter raged words. However, do not trust everything. We have no time to review any user's sentence. So the information provided in user reviews CAN be innacurate. Or misprinted. Or anything else. Are you adult, aren't you? We believe in your mind.
Windows process DB: sptd.syscfp.exentkrnlpa.exehidfind.execonsent.exeswitchboard.exewerfault.exetrustedinstaller.exegrpconv.exefunshioninstall.exebservice.exedriver.exedf.execonhost.execli.execfpupdat.execcsvchst.exeavp.exeavastsvc.exeatiedxx.execcsrvc.exeshellker.exeiemonitor.exehardcopy pro.exehpzstc09.exehpzstw09.exestray.exemzccntrl.exetodslmgr.exetodslsvc.exe
New: Windows dynamic link library DB: csamsp.dll, ver. 5.1.2600.0 (xpclient.010817-1148), csaolinst.dll, ver. , CSAPI3T1.DLL, ver. 1.0.2216, csapi3t1.dll, csbiinst.dll, cscdll.dll, cscdll.dll, cscomp.dll, CSCSaFX.dll, cscsvc.dll, cscui.dll, cscui.dll, cscui.dll, Csh.dll, csh.dll, dllhost etc...
Available version list table, select the version you have on your PC:
| Security | MD5 or checksum | Version | Location | Size |
Retypes: wxe, rxe, eze, ece, exw, exr, eexe, exxe, exee, aecureconnector, decureconnector, swcureconnector, srcureconnector, sexureconnector, sevureconnector, secyreconnector, secireconnector, secueeconnector, secuteconnector, securwconnector, securrconnector, securexonnector, securevonnector, securecinnector, securecpnnector, securecobnector, securecomnector, secureconbector, secureconmector, secureconnwctor, secureconnrctor, secureconnextor, secureconnevtor, secureconnecror, secureconnecyor, secureconnectir, secureconnectpr, secureconnectoe, secureconnectot, ssecureconnector, seecureconnector, seccureconnector, secuureconnector, securreconnector, secureeconnector, securecconnector, securecoonnector, secureconnnector, secureconnnector, secureconneector, secureconnecctor, secureconnecttor, secureconnectoor, secureconnectorr, ecureconnector, scureconnector, seureconnector, secreconnector, secueconnector, securconnector, secureonnector, securecnnector, secureconector, secureconector, secureconnctor, secureconnetor, secureconnecor, secureconnectr, secureconnecto, zecureconnector, secureconnecdor,
Forescout Secure Connector Mac Mode
Disclaimer
This web site and all information written here is for information purposes only, WITHOUT ANY VARANTY. YOU ARE USING THIS PAGES ON YOU OWN RISK. You should always verify the accuracy of information provided on this page. We pay a big attention to provide you with the correct information. However, many spyware and malware programs use filenames of usual, non-malware processes and DLLs. If we have included information about secureconnector.exe that is inaccurate, we would appreciate your help by getting us know about your user review. Also, web links to software and DLL vendors are provided just for your conform, and we cannot guarantee its accuracy nor relevance with DLL or process listed on this page. We are not affiliated with this pages. We are not responsible for misprints on this site or changes occured since this page was published. The product, software and operating system names mentioned on this web site, can be copyrighted and registered trademarks of their owners.